Cyber Security
The continuous growth of the internet has resulted in an increase in both opportunities and threats for organisations in ‘cyber-space’. Cyber security is one of the UK Government’s tier 1 threats and it is critical that cyber security risks are managed appropriately from Board level through to all relevant tiers in the organisation, and also into the supply chain.
Failure to manage cyber security risks might lead to cyber security breaches, reputational damage, distress to individuals and cost to your organisation.
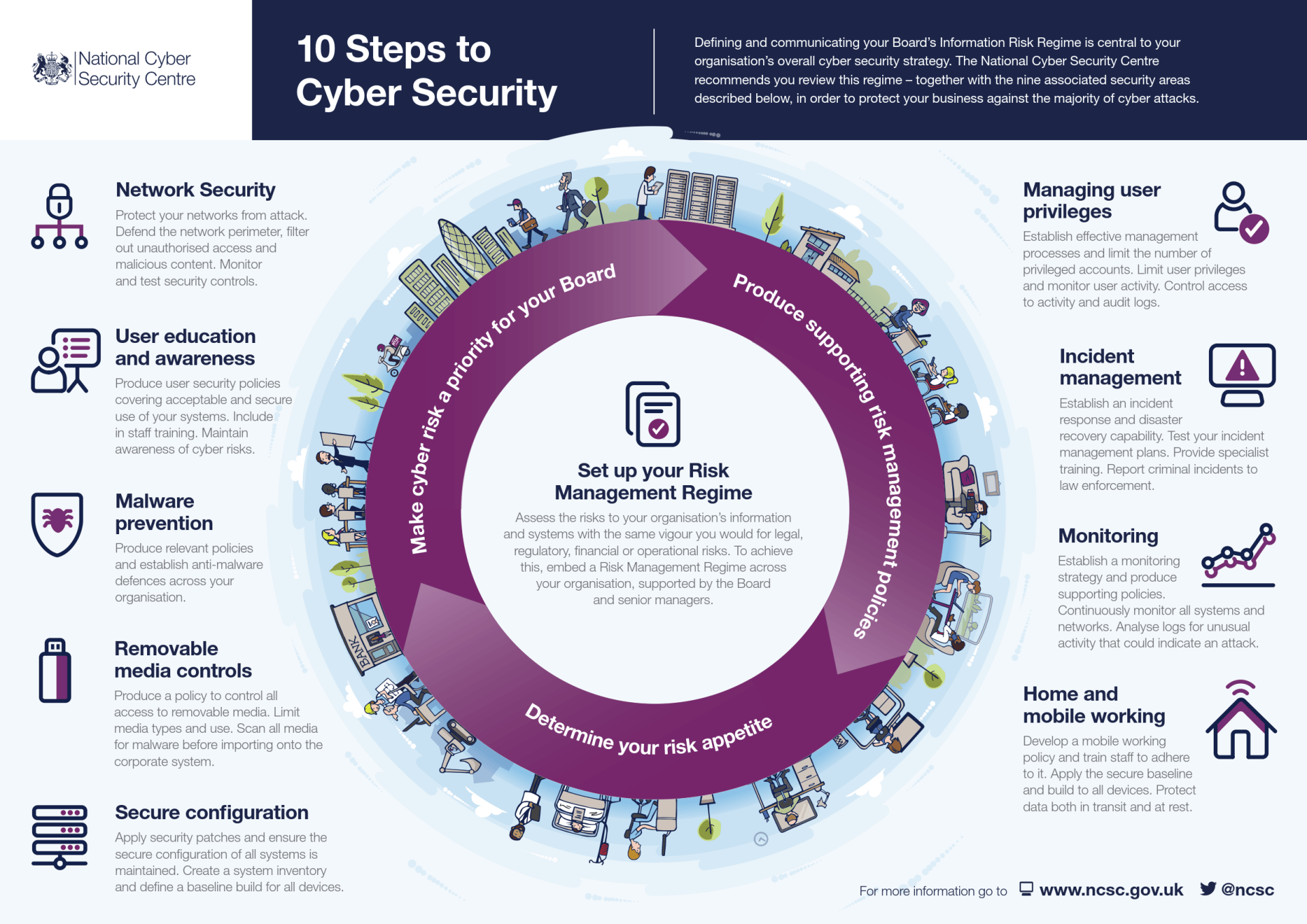
Cyber Security - the review of:
- Risk management regime and governance controls in place to minimise exposure to cyber security risk and ineffective policy implementation.
- Secure configuration around information systems to minimise exposure to cyber-attacks, thus increasing the risk of unauthorised access to systems and data.
- Network security controls in place to minimise compromising confidentiality, integrity or availability of information assets including customer identifiable data or other data, including commercially or politically sensitive data.
- Manage user privileges appropriately to minimise possible increases in the number of deliberate and accidental attacks.
- User education and awareness regarding procedures and policies around the use of digital, internet, social media and ‘cyber’ resources, to minimise exposure to cyber threats which increases the risk of having security of key data being compromised.
- Incident management capability in place to detect, manage and analyse security incidents to minimise the threat of a major disruption of business operations.
- Malware prevention controls in place and the effectiveness of minimising infections which can result in the disruption of business services, the unauthorised export of sensitive information, material financial loss and legal or regulatory sanctions.
- Monitoring ICT system processes in place, to minimise non-compliance with your corporate security policy and legal or regulatory requirements, or the possibility that attacks going unnoticed.
- Removable media controls in place to minimise the risk of exposure to the loss of information and the Introduction of malware.
- Home and Mobile working controls in place to minimise the risk of loss or theft of devices and information due to remote working risks.